Cloud
Storage Systems are Extremely Important for Business Continuity
In an era of increasing technological advancement, an important issue for enterprises and the key to maintaining business continuity is how to prevent important data from being accidentally lost due to human error, deliberately deleted or even stolen.
Can Your Business Protect Itself Against System Outages?
What Goals Should be Set?
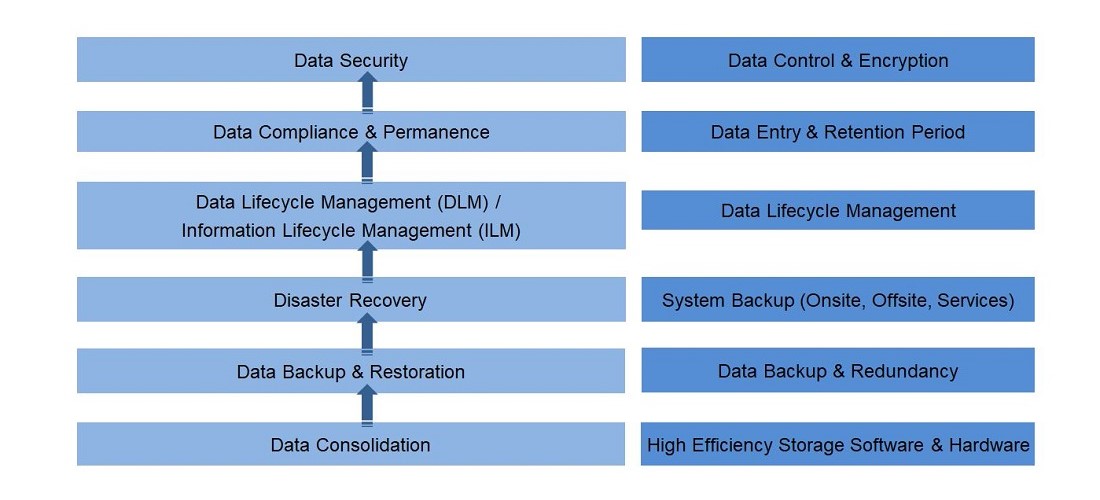
Classification & definition of data protection mechanisms

Data & system availability level definitions
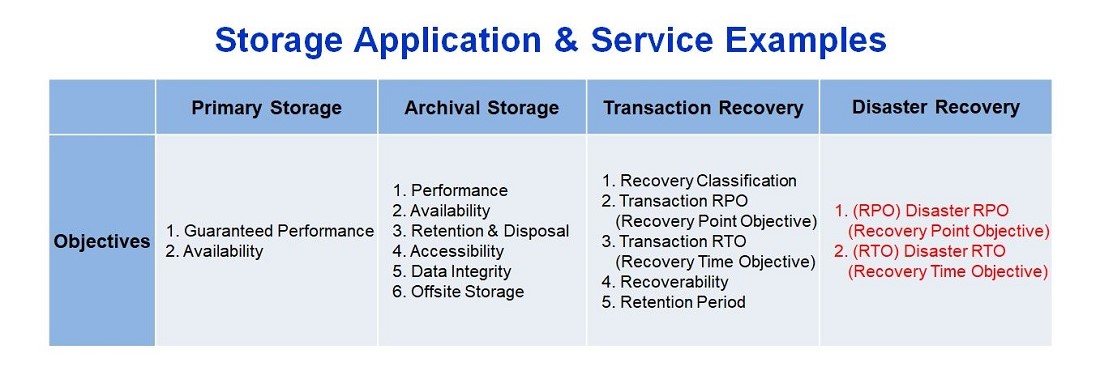
Classification & objectives of storage & backup systems
Who Should Be Responsible?
All the Money in the World Can’t Bring Back Lost Data
Data Storage is an Extremely Important Part of Business Continuity


The high performance transmission and processing requirements of storage systems used for Big Data & AI applications
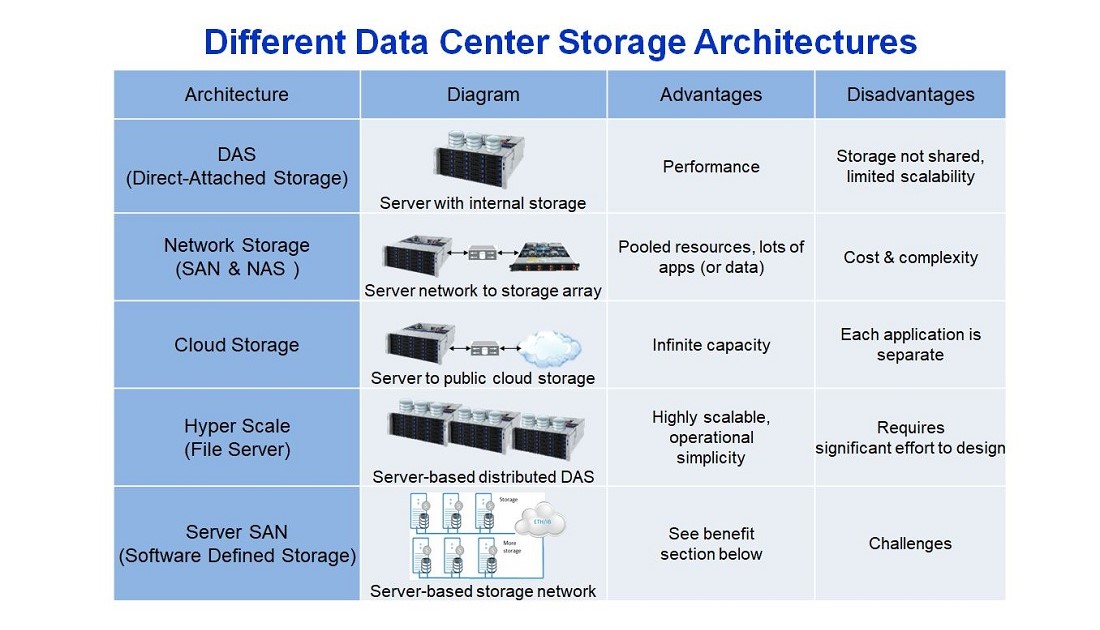
The 5 different types of data center storage architectures
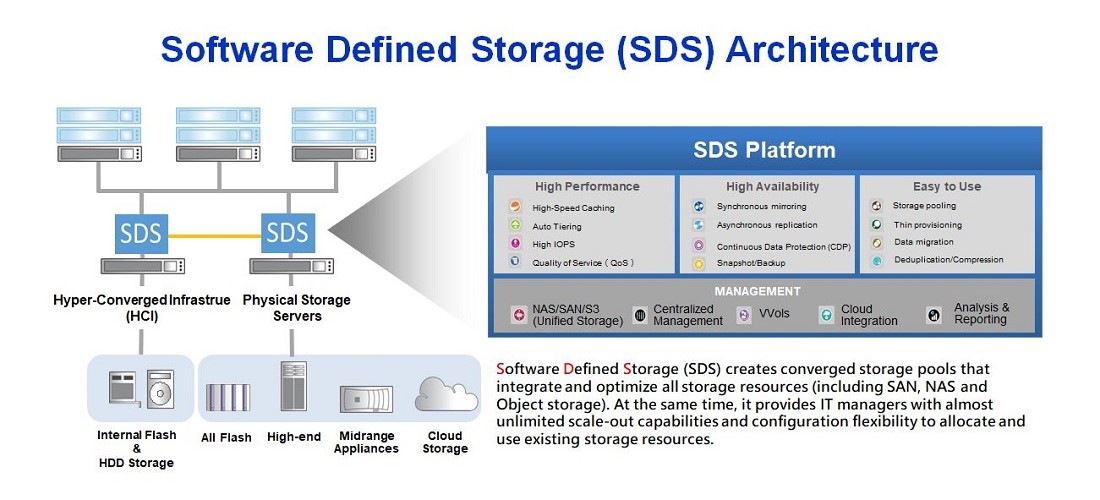
SDS meets the needs of cloud-based data centers

GIGABYTE Storage Server
Choosing the Right Partner is Extremely Important
GIGABYTE NVMe-Supported Server Model List
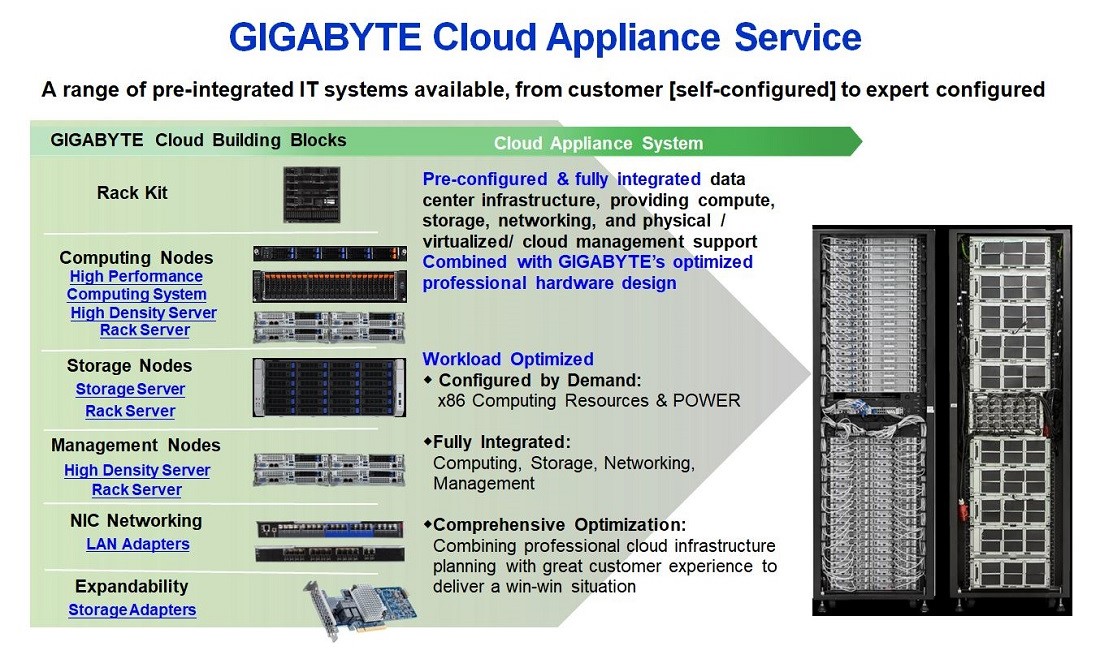
GIGABYTE Hardware for Cloud Appliance
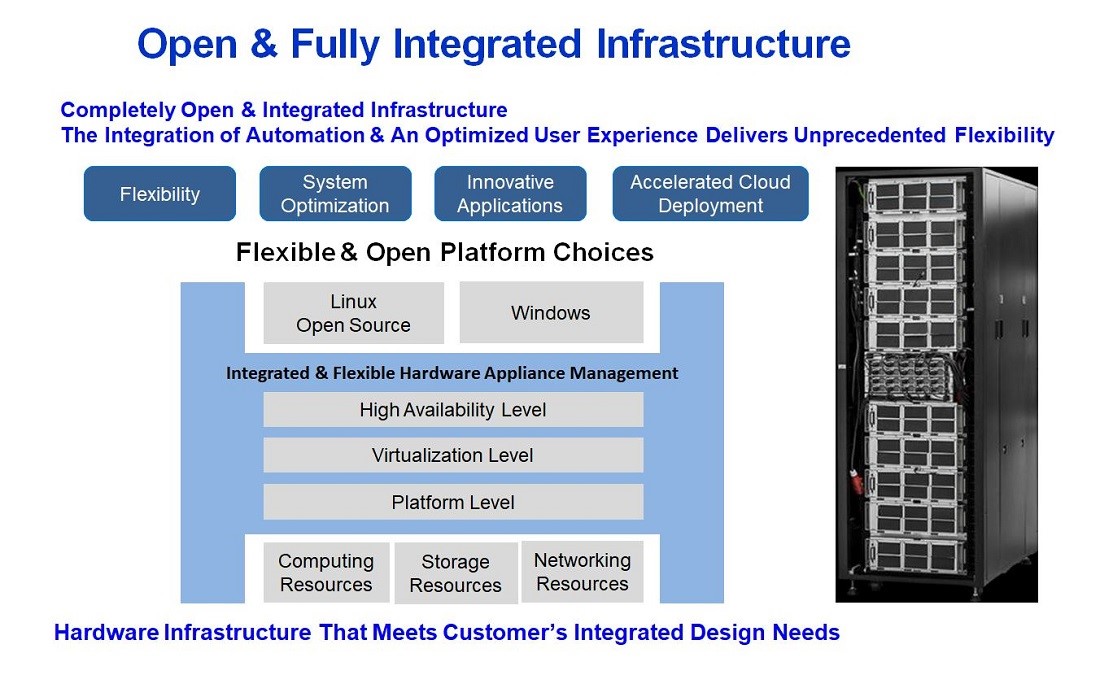
GIGABYTE’s x86 Open Rack Hardware Infrastructure
You have the ideas, we can help make it happen.
Get the inside scoop on the latest tech trends, subscribe today!
Get Updates
Get the inside scoop on the latest tech trends, subscribe today!
Get Updates















